Leading Penetration Testing Service Provider in Ireland
At CommSec, our team of certified and experienced professionals possesses an unwavering commitment to safeguarding your digital assets. We continuously enhance our expertise, staying abreast of the latest cybersecurity advancements and trends to ensure your organisation remains ahead of the ever-evolving cyber threat landscape. With over a decade of experience in the field, we have earned the trust of many large organisations across Ireland. Our comprehensive penetration testing services have empowered countless businesses to fortify their defenses and achieve unparalleled cybersecurity resilience.
What is Penetration Testing?
Penetration Testing, or a pen test for short, is a method of evaluating the security of a system or network by simulating an attack from malicious outsiders (who do not have an authorised means of accessing the organisation’s systems) and malicious insiders (who have some level of authorised access). The process involves an active analysis of the system for any potential vulnerabilities that could result from poor or improper system configuration, both known and unknown hardware or software flaws, or operational weaknesses in process or technical countermeasures.
CommSec’s Approach to Penetration Testing
At CommSec this analysis is carried out from the position of a potential attacker by our security consultants and can involve active exploitation of security vulnerabilities with a view to improving the security of your system or network. We can provide this service on its own or as part of our Security Assessment and Audit service. Security issues uncovered through the penetration test are presented to the system’s owner. Effective penetration tests will couple this information with an accurate assessment of the potential impacts to the organisation and outline a range of technical and procedural countermeasures to reduce risks.
Types of Penetration Tests Include:
- Network infrastructure testing
- Web application assessments
- Mobile application testing
- Active Directory assessments
- Assumed breach
- Restricted Desktop Break Out
Request a Quote
Some of our Customers
Benefits of Pen Testing
Fixes vulnerabilities before they are exploited by cybercriminals
Provides independent assurance of security controls
Improves awareness and understanding of cyber security risks
Supports PCI DSS, ISO 27001 and GDPR compliance
Demonstrates a continuous commitment to security
Supplies the insight needed to prioritise future security investments
Pen Test Customer Feedback
“CommSec provided an excellent service from beginning to end. They also provided us with a comprehensive and useful report. They worked seamlessly with our other vendors. I would have no hesitation in recommending them to any organisation that is looking for a cost-effective and comprehensive Pen Test”
Risk & Compliance Officer @ Affinity CU
We searched the market looking for a comprehensive IT penetration test provider and chose Commsec based on their pedigree as a Cyber Security provider. The tests itself was quick and we wouldn’t have even known it was happening! The final report was easy to understand and the lads were more than helpful in explaining any remediation.
IT Manager @ JVaughan Electrical
I just wanted to thank you and your team for the very professional job you did for us on the recent PEN Test. We look forward to working with you again in the future.
Rory Hopkins, Head of IT @ Kildare County Council
Commsec provided a thorough and professional penetration test on our applications. The whole interaction was flawless, and their findings and recommendations were invaluable. FarmVet Systems would highly recommend Commsec for their Penetration Testing Services
George Brownlee, CEO @ FarmVet Systems / VetImpress
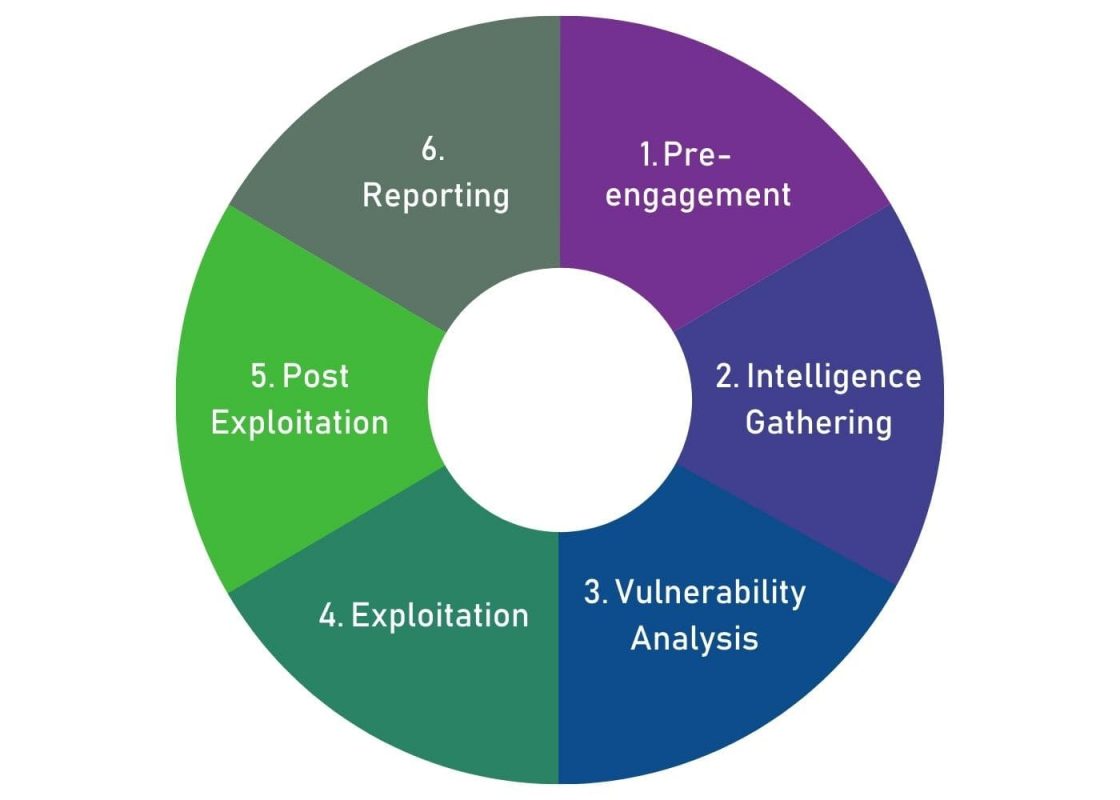
Our Pen Testing Methodology
Our methodology follows a six-step process that helps us ensure a thorough and effective evaluation of a client’s security posture.
- The first step is Pre-engagement & scoping, where we define the scope and objectives of the engagement, identify the assets to be tested, and agree on the testing methodology. This helps ensure that the engagement stays on track and the client’s expectations are met.
- Next is Intelligence Gathering, where we gather as much information as possible about the target network or application. This includes information about the technology used, the employees who have access to it, and any potential vulnerabilities.
- The third step is Vulnerability Analysis, where we use automated tools and manual techniques to identify vulnerabilities that could be exploited by attackers. We then prioritize these vulnerabilities based on their severity and the risk they pose to the client’s business.
- Once vulnerabilities are identified, we move on to the fourth step, Exploitation, where we attempt to exploit these vulnerabilities to gain unauthorized access to the target system. This helps us determine if the vulnerabilities can be exploited in a real-world scenario.
- The fifth step is Post Exploitation, where we assess the level of access we were able to obtain and explore the target system further to identify any additional vulnerabilities or weaknesses.
- Finally, we provide a comprehensive report in the Reporting step that includes our findings, recommendations for remediation, and a detailed breakdown of our testing methodology. This report helps the client understand their security posture and provides them with actionable steps to improve it.
Worried About Hidden Security Gaps? Uncover and Address Them with Confidence.
Contact us today to learn more about our penetration testing services and how we can help you safeguard your organisation’s digital assets.
Pen Testing Certifications
Our experienced team possesses the skills and experience to identify the latest threats. The teams certifications include:
- CREST (Globally recognised as the best certification for penetration testing)
- OSCP (Penetration Testing with Kali Linux) & OWSP (Foundational Wireless Network Attacks)
- GWAPT (Web app – SANS)
- CISSP (Certified Information Systems Security Professional -ISC2)
- CEH (Certified Ethical Hacker – EC Council)






Watch the Video
The Difference Between Penetration Testing and Vulnerability Scanning – all you need to know
FAQ's
What is penetration testing?
Penetration testing, also known as pen testing, is a process of assessing the security of a system, network, or application by simulating real-world cyber-attacks to identify vulnerabilities that could be exploited by malicious actors.
Why is penetration testing important?
Penetration testing is important as it helps organizations to identify and mitigate security vulnerabilities before attackers exploit them. It can also help organizations to comply with regulatory requirements and industry standards.
Who should conduct penetration testing?
Penetration testing should be conducted by trained and experienced professionals who have the necessary knowledge and skills to identify and exploit security vulnerabilities.
How often should penetration testing be conducted?
The frequency of penetration testing depends on various factors such as the size of the organization, the complexity of the systems and networks, and the industry regulations. In general, organizations should conduct penetration testing at least once a year or after significant changes to the systems and networks.
What types of penetration testing are there?
There are various types of penetration testing, including external network penetration testing, internal network penetration testing, web application penetration testing, wireless penetration testing, phishing penetration testing, IT health check, and ethical hacking.
What are the steps involved in a penetration testing process?
The penetration testing process typically involves five stages: reconnaissance, scanning, gaining access, maintaining access, and covering tracks.
Will penetration testing disrupt normal business operations?
Penetration testing may cause some disruption to normal business operations, especially during the initial stages of the testing process. However, professional penetration testing services should be conducted with minimal disruption to normal business operations.
What is the difference between a vulnerability assessment and penetration testing?
A vulnerability assessment is a process of identifying and documenting potential security vulnerabilities in a system, network, or application. Penetration testing goes a step further and attempts to exploit the identified vulnerabilities to determine their impact on the system or network.
What happens after a penetration test is conducted?
After a penetration test is conducted, the results are documented in a report that outlines the vulnerabilities that were identified and the recommended remediation measures. The organisation can then use this report to prioritize and address the identified vulnerabilities.
How can organisations ensure the effectiveness of penetration testing?
Organisations can ensure the effectiveness of penetration testing by selecting a reputable and experienced testing provider, defining clear testing objectives, establishing a clear scope of work, and monitoring the testing process to ensure that it is conducted in a safe and controlled manner.








