What is Threat Hunting?
Threat Hunting is the process carried to actively seek out threats on a network and identify malicious actors lurking on your network. Our SOC Team gathers a baseline of activity of your network to determine normal network activity. Our SOC analysts then kick off the hunt to find, track and hunt out a malicious actor. With real-time threat intelligence powered by AlienVault OTX our SOC Analysts siphon through your network traffic and host activity to compare it to the latest threats emerging. Throughout the hunting process our analysts use various procedures including Lockheed Martin’s Cyber Kill Chain, OODA Loop and Pyramid of Pain.
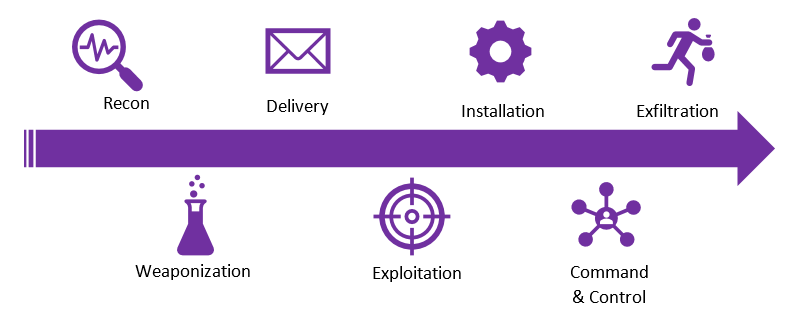
Why Threat Hunt?
There are numerous benefits to threat hunting by taking the proactive approach to look and seek out your threats. Threat hunting enriches SIEM alarming, new correlations can be created from the findings of the hunt. Underlying performance issues can also be discovered from threat hunting process. When threat hunting has been applied in your network it allows for new emerging threats to be thwarted quickly, whether it is an insider or outsider threat.
Therefore, by keeping on top of identifying new threats drastically helps your security posture across the network.
What is our Threat Hunting Procress?
Our SOC analysts actively seek out threats by hypothesising a question of what, why, where, when and how? By mining through security data applying hunting procedures and using the latest threat intelligence, new threats to your network can be stopped.
We apply threat hunting methods such as Honeytokens, Baselining, IOC based Hunting and Malware and Ransomware Remnants Hunting. We hunt out specifically target threats to your industry to help accurate locate and stop before a compromise or breach happens.
Baselining
After onboarding is completed and a network activity baseline is established. Our analysts then set out to hunt out and detect any malicious activity that is deviating away from normal activity. Establishing a baseline is important before conducting any threat hunting because some network activity may appear to be a threat and may not actually be classified as a threat on other networks.
Indicator of Compromise (IoC) Based Hunting
We receive the latest threat intelligence through our sources, as this intel comes into our SOC we compile these indicators of compromise and scan your network for these IOC’s. This allows us to report back to our customers with this information and initiate Incident Response to contain and eradicate these threats.
Malware & Ransomware Remnants Hunting
Any remnants left over from previous cases of malware or ransomware are also related to IOC hunting, Older artefacts can be gathered from endpoints. However, this may lead to the root cause of how and why a compromise happened in the past.

The 4 SOC Solutions IT Buyers Need to Know
In this blog post, the author explores the security technologies used by a SOC today and the differences between Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Security Orchestration, Automation, and Response (SOAR) and security information and event management (SIEM). The author also looks at the two different outsourced services, Managed Detection and Response (MDR) and SOC as a Service (SOCaaS), that wrap around these solutions.
Read moreget in touch
WHAT HAPPENS NEXT?
A member of our team will get back to you as soon as possible. They will find a suitable time to speak with you, answer any questions you have and help find the perfect solution to suit your requirements.

