
A Christmas breach
Santa’s list has just been stolen!
A list of all the children’s Personally Identifiable Information (PII) – Name, Address, details of good behaviour, best-friend facts, desired toys, and Santa’s favourite treat.
Bad news for Santa, who is now looking at GDPR fines, and bad news for the millions of kids who don’t know their PII has been stolen or that their Christmas will be ruined…
Breach happens!
More on this unfortunate theft later, we must first turn to the ongoing situation, which takes place every day for millions of grown-ups. PII is being stolen by the bucket-load and so much damage can be done with this information.
We have all been on websites or used services that have been hacked in the past.
Amazon, Microsoft, Facebook, Twitter – the biggest online names have been hacked, some of them on multiple occasions. This leaves our emails and user details in the hands of cyber criminals. All those phishing email and messages you get on a daily and weekly basis…? Now you know!
Often cases, the criminals who steal the data, display it publicly to highlight that a hack or breach has taken place, as in the famous Sony Pictures attack in 2014. In other cases, the stolen data is sold on to other thieves, who will use it for identity theft on the data owners – that’s you and me.
Breach payout
Most security professionals will try and explain the cost to your company due to a data breach. Let’s flip that on its head for a moment; what does it cost a cyber criminal to pay for the breached data?
The short answer is – very little.
A recent article from US Broadcaster PBS noted that “email dumps containing anywhere from a hundred thousand to a couple of million email addresses go for $10” on the dark web.
Privacy Affairs have compiled a fascinating Dark Web Price Index for 2021, which gives an insight into some of the PII and hacks being traded online.
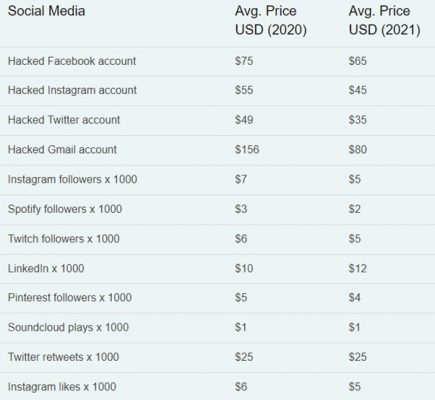
Personal data provides tangible value to cyber criminals.
It’s a sobering thought that a cybercriminal has your information and will use it for their own gain (and your pain). It’s also quite sobering if you are a business and an employer. A business will hold sensitive data and may hold and processes PII, on behalf of employees, customers, supply chains, etc. Some businesses will follow compliance and security standards in an effort to mitigate security risks. Security controls and best practices will be put in place and adhered to.
Assume Breach Position
With the best effort in the world, a business can still be hacked or breached. It may be a rogue insider or a committed hacker. It may even be an honest accident. It can take many days, weeks, or months to realise that a breach has occurred, and stolen data can cause many issues for the business, such as;
- Extorsion
- Brand and reputation damage
- Account takeover and future breaches
- Financial cost of regulatory fines
By many analyst and vendor calculations, it takes, on average, more than 200 days to identify a breach. In November of this year, GoDaddy became aware that a hacker had been in its network for more than 2 months. Today (Dec 13th), marks the anniversary of the massive SolarWinds breach report from FireEye (now Mandiant). We later learned that the attackers had access to information and systems for up to 9 months!
Breach awareness
Thankfully, businesses, large and small, can now utilise Digital Risk Protection. This is a means of proactively scanning the regular, deep and dark web. The value is realised in its continuous and proactive scanning for any information or data that may be related or relevant to a business – Sensitive files, email domains, login credentials, IP Addresses, email addresses, account numbers and more.
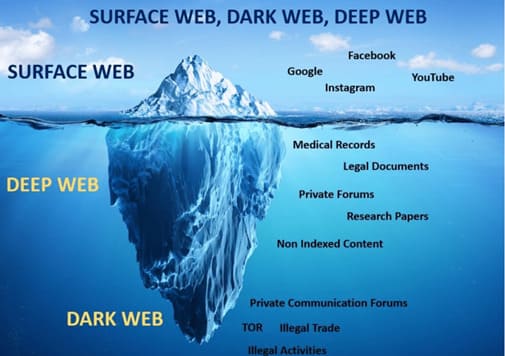
Positive scans will quickly alert on a breach, providing awareness and valuable remediation actions such as;
- Data take-down requests
- Incident Response on breached accounts and systems
- Improvements to bad password practice and cyber awareness
- Timely reporting of a breach
Our solution can also serve as a source of Threat Intelligence and can integrate with your current security and IT infrastructure.
For more on Dark Web Monitoring, Breach Alerting and Digital Risk Protection, contact [email protected] or visit our Dark Web Monitoring page.
We are currently running a free personalised digital footprint report to find out how exposed you are to digital risk.
I’m pleased to add, that through Digital Risk Protection, Santa was able to recover the stolen list and save Christmas. Santa is also scheduled for a security audit in the New Year!
Additional information
have I been pwned? is an official website to check if your email address or phone number has been in a data breach
The ‘World’s Biggest Data Breaches & Hacks’ on the Information is beautiful website, highlights attacks by sector and method over the past 17 years.
Ciaran Hayes is Business Development @CommSec.
