As technology advances, cyber-attacks have become increasingly frequent and sophisticated, posing a significant threat to all types of organizations. It is crucial for businesses to have a plan in place to detect, respond, and recover from a security breach. Unfortunately, over 77% of organizations do not have an incident response plan in place, leaving them vulnerable to attack (Ponemon Institute). With supply chain attacks on the rise, the risk of a security breach is higher than ever. In this blog post, we will explore the importance of the containment phase of the Incident Response plan and why it is now paramount during a cyber-attack.
What are the Phases of Incident Response?
Before diving into the details of the containment phase, let us first review the phases of the Incident Response plan. The NIST incident response lifecycle breaks incident response down into four main phases:
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Event Activities
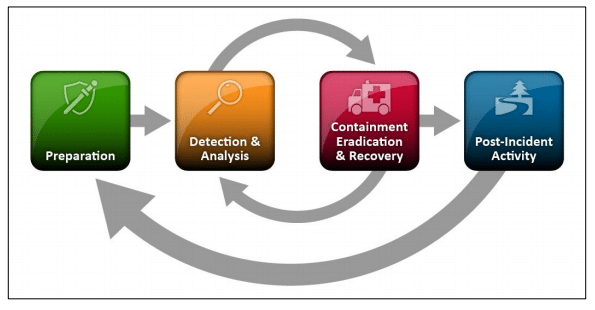
Each phase is critical to the overall success of an organisation’s ability to detect, respond, and recover from a cyber-attack.
Breakdown of the Containment Phase of Incident Response
The containment phase is the second stage in the Incident Response plan, following detection and analysis. The objective of this phase is to contain the attack and prevent further damage to the organisation’s systems, data, and reputation.
A recent study shows that nearly half (46%) of organisations are unable to contain a threat in less than an hour after the initial compromise, and most respondents identified 24/7 detection, response, containment, and remediation as a primary goal for 2021 (Kroll).
The containment phase consists of three steps:
- Isolate the system: The first step is to isolate the compromised system from the rest of the network to prevent further spread of the attack. This can be done by disabling network connections or removing the affected system from the network entirely.
- Identify the scope of the breach: The next step is to identify the extent of the breach. This includes identifying the data and systems that have been compromised and determining the source of the attack.
- Implement remediation measures: Once the scope of the breach has been determined, organisations can begin implementing remediation measures. This may include applying software patches, removing malware, or restoring data from backups.
Criteria for Incident Containment
Organisations must meet specific criteria to achieve incident containment. These include:
- Preventing further damage: The primary objective of incident containment is to prevent further damage to the organisation’s systems and data.
- Isolating the affected systems: As mentioned earlier, isolating the affected system is critical to preventing the spread of the attack.
- Identifying the scope of the breach: Organisations must determine the extent of the breach to effectively contain the incident.
- Implementing remediation measures: Once the scope of the breach has been determined, organisations can begin implementing remediation measures to restore their systems and data.
- Minimising impact: Incident containment also involves minimizing the impact of the attack on the organisation’s operations, customers, and reputation.
- Maintaining business continuity: Organisations must ensure that their business operations can continue while the incident response plan is executed.
Meeting these criteria can help organisations achieve robust incident containment.
Strategies for Effective Containment of Security Incidents
To achieve effective incident containment, organisations can implement the following strategies:
- Rapid response: It is crucial to respond to a security incident as quickly as possible to prevent further damage.
- Isolate affected systems: As mentioned earlier, isolating the affected systems is critical to prevent the spread of the attack.
- Block malicious activity: Organisations can use firewalls, intrusion detection systems, and other security tools to block malicious activity.
- Monitor the network: Organisations should continuously monitor their network for suspicious activity to identify and respond to potential security incidents.
- Leverage threat intelligence: Threat intelligence can provide valuable insights into the latest attack techniques and trends, helping organisations better prepare for and respond to security incidents.
- Train employees: Well-trained employees can become a security asset. Regular training and education are essential to help employees identify and respond to security threats.
Implementing these strategies can help organisations achieve effective incident containment and mitigate the damage caused by a security incident.
Threat Intelligence and Incident Containment
Threat intelligence can play a vital role in incident containment. By monitoring the latest threat intelligence, organisations can better understand the latest attack techniques and trends, helping them better prepare for and respond to security incidents.
Threat intelligence can also provide organisations with actionable insights into potential threats, enabling them to take proactive steps to prevent incidents from occurring in the first place.
How to Execute the Containment Phase of Incident
To execute the containment phase effectively, organisations should follow these steps:
- Gather the incident response team: The incident response team should be assembled to lead the containment effort.
- Identify the affected systems: Determine which systems have been compromised and isolate them from the network.
- Gather evidence: Collect evidence related to the incident, including system logs, network traffic data, and other relevant information.
- Determine the scope of the breach: Determine the extent of the breach to help prioritize the response effort.
- Implement remediation measures: Apply software patches, remove malware, or restore data from backups.
- Verify containment: Once the remediation measures have been implemented, verify that the incident has been contained.
💡Tip: One thing people forget quite often is to have a hard copy of the incident response plan. No good if it is sitting on a system that is out of action.
Conclusion
The containment phase is a crucial aspect of the Incident Response plan. Organisations must meet specific criteria to achieve incident containment, including preventing further damage, isolating affected systems, identifying the scope of the breach, implementing remediation measures, minimizing impact, and maintaining business continuity.
To achieve effective incident containment, organisations can implement strategies such as rapid response, isolating affected systems, blocking malicious activity, monitoring the network, leveraging threat intelligence, and training employees.
By following the steps outlined in this blog post, organisations can achieve robust incident containment and mitigate the damage caused by a security incident.
Further reading: Managed Detection & Response service and CISO as a Service

