Cyber security is one of the most important topics in today’s business environment as cyberattacks are growing at an exponential rate, and small businesses and large businesses alike have fallen victim to them. With hackers and their tools getting more sophisticated every day, it is becoming increasingly difficult to protect yourself from them. SMEs can still do their bit to arm themselves with cost-effective security plan to reduce the risk of compromise.
Cyberattacks against European companies are now more frequent. With at least 80% of companies in Europe having experienced at least one cybersecurity incident over the last year (EESC), the average number of cyberattacks and data breaches increased by 15.1% from the previous year in 2021 (ThoughtLab), and 69% of European SMEs have either no or only a basic understanding of their exposure to cyber risks (Marsh).
Small and medium-sized enterprises (SMEs) constitute the weak link in cyber-attacks. They face rising threat levels and pay the highest price for operating online. Despite growing threat levels, they remain ill-prepared for cyberattacks, showing lower than average maturity levels. SMEs struggle not only due to a lack of awareness but also because they perceive cyber security as a costly endeavour.
Having an effective cyber security plan in place will help you:
- Know the right protections are in place and are working, which will reduce the risk of a breach for your business
- Have the confidence that your employees only have access to what they need to do their jobs and have peace of mind that they are conducting their work safely
- Know what technology assets you have and that they are protected by multiple layers of security
- Get better ROI on investments in technology and have less waste because you know what is important
- Help satisfy the requirements set out by cyber insurance underwriters
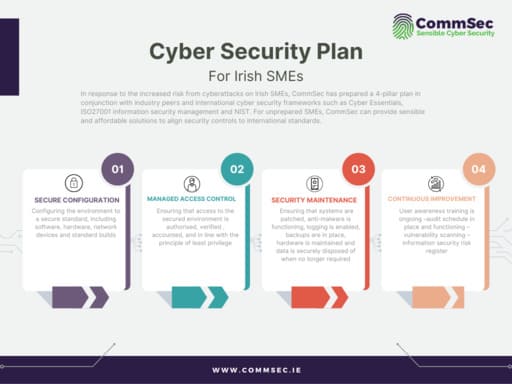
Work is underway to introduce a standard set of cyber security controls for Irish businesses. CommSec has helped develop a 4-point advisory plan in conjunction with industry peers and based on international standards such as ISO27001 and Cyber Essentials, to help SMEs implement sensible security controls and reduce the chances of a successful attack.
The cyber security plan is made up of several controls contained within four critical areas or pillars:
- Secure Configuration
- Managed Access Control
- Security Maintenance
- Continuous Improvement
1. Secure Configuration
Configuring the IT (Information Technology) environment to a secure standard, including software, hardware, network devices and standard builds.
Web server and application server configurations play a crucial role in cyber security. Failure to manage the proper configuration of your servers can lead to a wide variety of security problems. Computers and network devices should be configured to minimise the number of inherent vulnerabilities and provide only the services required to fulfil their intended function.
This will help prevent unauthorised actions from being conducted and will also ensure that each device discloses only the minimum information about itself to the Internet. A scan can reveal opportunities for exploitation through insecure configuration.
Computers are often not secure upon default installation. An ‘out-of-the-box’ set-up can often include an administrative account with a standard, publicly known default password, one or more unnecessary user accounts enabled (sometimes with special access privileges) and pre-installed but unnecessary applications or services.

2. Managed Access Control
Ensuring that access to the secured environment is authorised, verified, accounted for, and in line with the principle of least privilege.
It is important to keep access to your data and services to a minimum. This will help to prevent a criminal hacker from being presented with unrestricted access to your information. Obtaining administrator rights is a crucial objective for criminal hackers, allowing them to gain unauthorised access to applications and other sensitive data. Convenience sometimes results in many users having administrator rights, which can create opportunities for exploitation.
User accounts, particularly those with special access privileges, should be assigned only to authorised individuals, managed effectively, and provide the minimum level of access to applications, computers, and networks. It is important to only give users access to the resources and data necessary for their roles, and no more. All users need to have unique accounts and should not be conducting day-to-day tasks such as invoicing or dealing with e-mail whilst logged on as a user with administrator privileges which allow significant changes to the way your computer systems work.
User accounts with special access privileges (e.g., administrative accounts) typically have the greatest level of access to information, applications, and computers. When attackers access these privileged accounts, they can cause the most amount of damage because they can usually perform actions such as installing malicious software and making changes. Special access includes privileges over and above those of normal users.
If you are not already using two-factor authentication (2FA) or MFA (Multi-factor authentication) to protect your organisation, now is the time to get started. MFA means that a user authenticates with more than one type of authentication, such as a password and access to a mobile device like a smartphone or token. We are always surprised by the number of SMEs who do not have MFA turned on and when done so can block 99.9% of automated attacks (Microsoft).
Password management is a system that allows users to store and access passwords securely. Password management is defined as a system that facilitates a simple, secure way to store passwords and access them quickly when required. Today, password management is a critical part of the IT policy of most organizations.
Password managers generate strong passwords, store them securely, help you keep track of any accounts you have online (so you do not use the same password on each one) and can also help recover your other passwords if needed.

3. Security Maintenance
Ensuring that systems are patched, anti-malware is functioning, logging is enabled, hardware inventory is enabled, backups are in place, hardware is maintained, and data is securely disposed of when no longer required.
All devices and software are prone to technical vulnerabilities. Cybercriminals can rapidly exploit vulnerabilities once they have been discovered and shared publicly. Criminal hackers exploit known vulnerabilities in operating systems and third-party applications if they are not properly patched or updated. Updating software and operating systems will help to fix these known weaknesses. It is crucial to do this as quickly as possible to close any opportunities that could be used to gain access.
To protect your organisation, you should ensure that all your software is always up to date with the latest patches. If you are using an operating system which is no longer supported, (e.g., Microsoft Windows XP/Vista/2003/7/8 or macOS El Capitan, Ubuntu 17.10), and you are not being provided with updates from another reliable source, then you will not be eligible for certification from international security standards. Mobile phones and tablets should also be in consideration and must also use an operating system that is still supported by the manufacturer.
Having Up-To-Date antimalware is important. Antimalware is a type of software program created to protect IT (Information Technology) systems and individual computers from malicious software, or malware. Antimalware programs scan a computer system to prevent, detect and remove malware. Again, having effective antimalware on mobile devices is an often forgotten about but important part of basic security controls. Mobile device protection can block malicious apps, detect spyware, and thwart phishing attacks.
A fundamental element of any cybersecurity program is a comprehensive inventory of all IT assets across the enterprise. Without a comprehensive knowledge of all the systems, programs, patch levels, and types of information within its area of responsibility, no organization can plan adequate defences from a coordinated cyberattack. You cannot secure that which you don’t even know exists. The best solution is to use a platform that allows continuous and automatic discovery of all devices, applications, users, and their associations. Automation is the only effective way to understand, manage, and secure a wide range of assets. Choosing a manual solution will result in errors and is a time-consuming process which will leave organisations open to hidden risks and vulnerabilities.
Back up your data! Nothing is more frustrating than when your data is lost, corrupted, or stolen because it was not backed up. Plus, even if you have a great backup strategy in place, backing up to the cloud is just one more thing to make sure you are doing. But backing up your data also offers peace of mind and saves time for your IT (Information Technology) team, which can then be allocated elsewhere.
Ensure you have regular back-ups in place and that you evaluate them frequently to make sure the back-up was completed successfully and is not corrupt. Sometimes updates to software can change a setting and your back-ups do not complete. It is good practice to back up your website too so that if you need to reinstall it you have the data ready to go. This will save you hours of heartache if your website encounters a problem or becomes compromised.

4. Continuous Improvement
Cyber threats are ever evolving by their nature. Hackers are constantly refining their activities and trying new ways to compromise people and businesses. To keep on top of evolving threats you must implement continuous improvements in the following areas:
Educate your employees
IT security has become an increasingly difficult battle with hackers trying new ways every day to penetrate your network or compromise personal information on social media sites such as Facebook, Instagram, and LinkedIn. It is important for every business to have a basic cyber security awareness training program, platform software and education for employees. All employees must be trained in cyber security awareness and build the knowledge on what to look out for when being targeted by hackers using a phishing email. Having a well-trained workforce can be one of the best cyber defences a business has.
An effective training program includes engaging video training modules, follow-up quizzes to evaluate knowledge and email phishing simulation campaigns to identify where gaps in knowledge occur. Having a security awareness platform in place will ensure your business gets regular reports and training records are stored for all employees.
Vulnerability Scanning
Vulnerability scanning is an automated process that identifies your cyber security weaknesses with network infrastructure, applications, or websites. Like a Penetration Test which is a manual security test, a vulnerability scan is an automated program that scans IT infrastructure for known and zero-day vulnerabilities. Effective vulnerability scanning gives a continuous and structured picture of your digital assets and their cyber security, and the reporting gives you remediation advice to fix the vulnerabilities, lessening the risk of exploitation. Running regular scanning is advised.
Cyber Security Audit (Advanced)
A cyber security audit is a comprehensive review of an organisation’s IT infrastructure. Audits ensure that appropriate policies and procedures have been implemented and are working effectively. The goal is to identify any vulnerabilities that could result in a data breach.
Information Security Risk register
A risk register is an information repository an organisation creates to document the risks they face and the responses they are taking to address the risks. At a minimum, each risk documented in the risk register should contain a description of a particular risk, the likelihood of it happening, its potential impact from a cost standpoint, how it ranks overall in priority relevant to all other risks, the response, and who owns the risk.
Risk registers are useful information-gathering constructs: They help senior leaders see the full spectrum of their organisation’s significant risks and understand how to best manage the risks to achieve organisational objectives.
Incident Response Plan
An Incident Response Plan (IRP) serves as a blueprint, outlining the steps to be followed when responding to a security incident. Think of the IRP as a set of guidelines and processes your security team can follow so threats can be identified, eliminated, and recovered from. It is an essential tool for minimizing damage caused by threats, such as data loss, loss of customer trust, or abuse of resources. With a robust IRP, your company’s team can respond quickly and more efficiently against any type of threat.

4 Pillar Cyber Security Plan – Infographic
Download the 4 Pillar Cyber Security Plan (PDF)
How can CommSec help?
CommSec is a leading cyber security managed security service provider. Established in 2013, CommSec was borne out of the need for affordable and sensible cyber security for SMEs. We use the best of technology and experienced security professionals to deliver unrivalled service. To get started, contact us, and tell us about your business and your current security challenges.

